What was the most difficult part of the course? Anything you'd do differently?
Blogging:
The most difficult portion of this course was ... the blogging portion! While I am not very talented with coming up with new topics, I felt that keeping focused on one target topic was difficult to do even when I didn't have to go through and get sources! The challenge was more with having too much freedom and wondering how to be creative enough with pictures, videos, diagrams, etc.
While this was the difficult part, I would certainly not get rid of it or remove it from the course. I do believe that most folks coming up with technology are "gun-shy" from making posts like this online with their name tied to it. Everything on the internet is now permanent --meaning that these very sentences can be used to reference my name. So speaking with a lesser form of understanding on a topic or from a position/mindset can come back and give someone an opinion of us. That all being said, I believe that not doing this limits the creativity and willingness to address issues as they arise from a collaborative approach. I may not have the right direction or ability to fix something, but I could start talking with someone who has an idea that can move many readers in the right direction to solve security related issues. That is the beauty of blogging.
Capstone Assignment:
The capstone assignment was all around an interesting assignment that challenges students to overcome a typical 3rd party security consult for an organization. This semester, it made us think like we were on the job and working with an audience/customer that didn't know the whole world of cyber security. This required us to analyze everything as a IT person while presenting it as a marketer (knowing the audience, speaking at their level of understanding and verify they can interpret/ingest everything).
Overall, the project required knowledge of how to assess an environment, create visio diagrams, perform risk assessments, looks at lists of vulnerabilities, cost analysis, likelihood, etc. However, there was a good deal of overlap from the risk assessment course (in terms of the target case environment). I think that we should have had a different environment so the risk assessment tables would be different. While there were a couple changes, this was not enough to stimulate as much of a deeper dive. I also think that the client presentations should have some form of template. The assumption is that we are supposed to be able to provide some sort of consulting services, and I think a course that worked more to translate IT into the business world would be useful. Such as a half way course for integrating IT with a MBA-like or CIO role.
One thing that I wish we could change is the way discussion posts are done. I wish that there was a better way for us to communicate. I often times don't appreciate how shallow conversation posts are and I don't think they stimulate critical thinking for most folks. I wish that there were some sort of seminar hours where we could all get together on a web chat and talk with one another and the professor. I understand that the most prominent aspect of an online education is the flexibility, but perhaps do a chat sort of like the 'Marco Polo' application. This is where everyone is able to take and save/submit clips to perform a discussion in person over the course of a week. I think that would kill the redundancy and require folks to think more about cheesy posts.
Well, I believe this is my last post for my graduate degree =D
Cyber Security for Today
Saturday, February 23, 2019
Saturday, February 16, 2019
Week 10: Action Plans Galore
When looking at any system, most folks focus on the bad ugly parts that stick out. There is a certain level of shock and awe that really draws folks. I'm not sure if that is our way of coping with the failures of ourselves and others, or a means to distract us from the work ahead. Inevitably, the any sane person or organization will take those shortcoming and implement a fix to correct those issues, right? Actually, in my experience, this is where more folks shy away because it means work is required. Work that includes thinking or engineering a solution, spending money and time, and jeopardizing their stature if the solution fails and wastes all of the aforementioned. When I see folks shy aware on my projects, I gently remind them that on my staff I care more about folks that are willing to make mistakes (learn from them and pivot for another solution) rather than those that are too cautious and freeze. It is usually pretty easy to spot folks that will just burn those whole place down, but a workforce really needs folks that are able to take risks and think outside the box.
However, the most beautiful thing is to look at the problem and start engineering a solution! Even if there is a "top 10 solutions for (x) problems" guide out there, you are still implementing a solution for your environment. This means that at some point, sure varying levels of implementation, the team has to do SOMETHING to provide a fix for an issue. Most of the time, providing a fix for an issue is always a good thing, whether you a making a profit or providing protection. But as John Gibson states about half way into the video below, security is a Business Issue not an IT issue! This means that yes it will impact the business in some way. Decisions need to be made from ethical and financial standpoints that are outside the usual scope of the CTO.
So what does that mean for us "Action Planners"? It means that we need to be able to find solutions or options that vary in size, cost, scope, implementation, etc and provide that to the shot callers so that they can make the best decision for the organization. Sometimes we may lean towards one direction, but that doesn't mean that they are wrong. Much like not knowing the workload or priorities of other staff members, we don't know everything that they are weighing against up there around the board of directors table. However, from our level if we can take action, think, and provide a myriad of potential solutions in our action plans, then they are much more likely to make a sound decision for the betterment of the organization as a whole.
However, the most beautiful thing is to look at the problem and start engineering a solution! Even if there is a "top 10 solutions for (x) problems" guide out there, you are still implementing a solution for your environment. This means that at some point, sure varying levels of implementation, the team has to do SOMETHING to provide a fix for an issue. Most of the time, providing a fix for an issue is always a good thing, whether you a making a profit or providing protection. But as John Gibson states about half way into the video below, security is a Business Issue not an IT issue! This means that yes it will impact the business in some way. Decisions need to be made from ethical and financial standpoints that are outside the usual scope of the CTO.
Sunday, February 10, 2019
Week 9: Spectre and Meltdown!
Meltdown|Spectre: The physical vulnerability that emits OS level data
First and Foremost, we have to give this up to Google's Project Zero for finding and publicly posting this massive flaw. There is no doubt in my mind that they were also affected by the huge vulnerabilities, but even this massive Tech Giant felt that it was critical that the world new about Meltdown and Spectre. Not only were they identifying this, but there were telling the world exactly where to start looking because this is a whole new vector or perspective of vulnerabilities. Much like the first gold rush in the US, once one nugget was found ... it caused so many others to start looking for more!
Here is there post from January 3rd, 2018: https://googleprojectzero.blogspot.com/2018/01/reading-privileged-memory-with-side.html
So recently, I learned a good deal more about Spectre and Meltdown and I found it pretty fascinating. The overall process reminded me of a dumpster diving. At one point in time, folks didn't really concern themselves with what they threw away. They would throw away unopened credit card offers, bank statement that they finished reviewing, or even throw-away old cards/checks without disfiguring them beforehand.
On a bit more technical level, I found this site absolutely useful: https://www.csoonline.com/article/3247868/vulnerabilities/spectre-and-meltdown-explained-what-they-are-how-they-work-whats-at-risk.html
The overall gist here is that these side-channel techniques are able to access data that they don't have permissions to because the data is saved in several locations that are accessed faster/easier than the CPU is able to do a permissions check on.
There are two compute mechanisms at play here. The first is the CPUs ability to front load operations and data while it is waiting for another longer process to complete and tell it what to do.
For instance, when working on building a house we are waiting on supplies to be delivered before completing the framework on the doors in the master bedroom. These supplies can either come in as aluminum or wood. Regardless of which they come in as, we can still go through and measure out what the cuts would be (thicker cuts for wood and thinner for metal). When the materials arrive we would throw away the measures for the materials we aren't using right? But why did we go through this process? Well waiting for supplies to check measurements would take longer because we have to wait for the supply deliver. Figuring out the measurements for both scenarios beforehand is way faster and we can just discard the wrong measurements. Critically, before the supplies ever arrive at the jobsite, any person can come over and ask for both sets of measurements.
In these side-channeled memory attacks, when a process is running larger math problems, speculative execution is cramming in several scenarios of data calls that may or may not be used. And the data sets that aren't used are then offloaded improperly. Even while the process is waiting for the larger math problem to complete, a smaller/faster process may sweep in and ask about both data sets and aggregate enough information before the discard before the processor ever determines if the process has access to that data.
Week 8: audit process v. threat model
In my current course for learning how to analyze an environment and apply a security posture for the current vulnerabilities, threats, exposures, etc we have been working on how to create and apply threat models.
During the first few weeks we learned about threat models in general and how to create our own. Per usual, there were a couple industry standards out there; however, there was a point be driven... Threat models are constantly being updated and tweaked either for a specific project, a target audience, or because there a new vector to account for.
Initially, I thought the threat model was synonymous with the normal IT audit life cycle. The audit life cycle goes through and identifies assets/systems/processes to create a baseline. Then it will go through and analyze the state of each of those items to annotate the everything wrong. Then they will go through and generate a report about each of those with recommendations and submit that to the customers. Some of these reports will then show recommendations -- showing the same value vs likelihood vs risk exposure, etc.Then they will demonstrate how these items can be monitored over the length of time before the next audit.
So what I'm curious about is, which came first? The audit process or the de facto threat model? Will the audit process change if the de facto threat model changes? I assume so and it'll be a sweeping change with wide adoption.
I have learned that there are additional steps and tools that can be used to assist in providing this report. The culmination of these tools has altered the presentation at the end of this and perhaps there is the answer. Perhaps the audit is more geared towards the department level and operations while the threat model is more geared towards senior leadership and executives at the company.
The tools that we have used more for this course is like flow diagrams to show a very simplistic overview of how a system is or should operate. Working through STRIDE, to make it stick and be visually appealing is a great example.
 |
| https://www.researchgate.net/publication/283205029/figure/fig6/AS:325314161987590@1454572348624/Relation-between-STRIDE-security-attributes-and-security-service-for-HTN.png |
Week 7: scripting
Week 7:
Programming Humor Meme of the week --

I've been told that my power shell cohorts don't appreciate my naming conventions. They prefer to use larger variable names that have something specifically tied to that script. I don't like that and I prefer to have it simplistic so I can focus on the functionality of what my scripts are doing. This meme kinda reminds me of that. It shows that someone out there likes to use their brackets on the site. Personally -- they're dumb and this is terrible >:-D but to each their own.
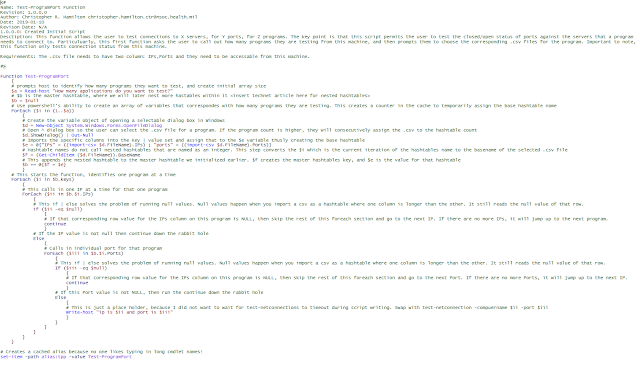
Here is a quick example of the format I use for my scripts (this was a teaching element I used for one of my teams on powershell's netsted hashtables ):
To me, the use of variables in a powershell script can sometimes lead the reader astray. If the reader needs some assistance with a line, that is what comments are for. When jumping through so many different scripting languages, I feel that it is easier to utilize a similar format across them all for familiarity.
Powershell is important because it is the new Microsoft language that can fully interact with everything internally. They are gearing themselves to an operating system that can be manually operated through a user-friendly language. Whats more is that they permit users to create their own cmdlets, functions, modules, and packages.
How does this tie into security? How about the PowerShell Empire? This was a site that started the push for using powershell to get information about local/remote system to help test security mechanisms. While the original site is no longer maintained (http://www.powershellempire.com/?page_id=110), there is a github for PowerShellEmpire 3 (https://github.com/EmpireProject/Empire/wiki/Quickstart).
Powershell Empire 3 from github is this massive module that has tons of powerhell variants for things like code execution, gathering credentials, exploitation, ex-filtration, recon, and much more. Here is a more recent how to video using it:
Programming Humor Meme of the week --

I've been told that my power shell cohorts don't appreciate my naming conventions. They prefer to use larger variable names that have something specifically tied to that script. I don't like that and I prefer to have it simplistic so I can focus on the functionality of what my scripts are doing. This meme kinda reminds me of that. It shows that someone out there likes to use their brackets on the site. Personally -- they're dumb and this is terrible >:-D but to each their own.
Here is a quick example of the format I use for my scripts (this was a teaching element I used for one of my teams on powershell's netsted hashtables ):
To me, the use of variables in a powershell script can sometimes lead the reader astray. If the reader needs some assistance with a line, that is what comments are for. When jumping through so many different scripting languages, I feel that it is easier to utilize a similar format across them all for familiarity.
Powershell is important because it is the new Microsoft language that can fully interact with everything internally. They are gearing themselves to an operating system that can be manually operated through a user-friendly language. Whats more is that they permit users to create their own cmdlets, functions, modules, and packages.
How does this tie into security? How about the PowerShell Empire? This was a site that started the push for using powershell to get information about local/remote system to help test security mechanisms. While the original site is no longer maintained (http://www.powershellempire.com/?page_id=110), there is a github for PowerShellEmpire 3 (https://github.com/EmpireProject/Empire/wiki/Quickstart).
Powershell Empire 3 from github is this massive module that has tons of powerhell variants for things like code execution, gathering credentials, exploitation, ex-filtration, recon, and much more. Here is a more recent how to video using it:
Wednesday, January 23, 2019
wk 6 - Source review TheHackerNews.com
To analyze and review the sources stated in wk-2, the one that I have actually continued to use is https://thehackernews.com. This site has easy reading and doesn't seem to over-exaggerate articles to meet a steep publish quota.
Looking at today's article,
Looking at today's article,
Someone Hacked PHP PEAR Site and Replaced the Official Package Manager
it has several appealing elements to those writing reports. Their style shows what the content is, how that appeals or affects people and their systems, and then provides sources for nearly everything. The majority of this article goes on to explain what PHP repositories are, why they are used, and how expansive the PHP PEAR site was for a global user base. The real beauty of their reports is that they provide a semi-technical way of bringing the reader up to speed on the technology before jumping into the security breach. In this article alone, there are five sources scattered throughout and they are not all centered around one specific section. This provides well-founded coverage.
To look closer at another article, DHS Orders U.S. Federal Agencies to Audit DNS Security for Their Domains by Swati Khandelwal, it reviews an order by the Department of Homeland Security to strengthen the government's DNS standards and perform audits to validate those settings. Swait provided a link to DNS hijacking, and a good description of what that is and how it relates to this DHS directive. Swati also gave a link to the DHS directive site to provide legitimacy to the article which gives the reader the ability to follow up on everything. As a student, that provides me a means to find additional information and provided this is a direct source for a citation instead of just quoting the article. Additionally, the article covers several other related segments such as other sites that were recently hijacked because of poor DNS security and specific details for the audit requirements.
https://thehackernews.com/2019/01/dns-hijacking-cyber-attacks.html
https://thehackernews.com/2019/01/php-pear-hacked.html
Wk 5 - Holiday hack challenge Write-Up 2018
Here is my write-up for the SANS 2018 Holiday Hack challenge, which is a free public competition to complete as many challenges as possible for some free prizes. During this challenge, my most difficult portion was the last section: sql injection!
1.
Orientation Challenge
a.
Challenge
What phrase is
revealed when you answer all of the questions at the KringleCon Holiday Hack History kiosk inside the
castle? For hints on achieving this objective, please visit Bushy
Evergreen and help him with the Essential Editor
i.
Key: Happy Trails
b.
Answer all questions correctly to get the secret
phrase!
i.
Question 1
- In 2015, the Dosis siblings asked for help
understanding what piece of their "Gnome in Your Home" toy?
- Key: Firmware
ii.
Question 2
- In 2015, the Dosis siblings disassembled
the conspiracy dreamt up by which corporation?
- Key: Antas
iii.
Question 3
- In 2016, participants were sent off on a
problem-solving quest based on what artifact that Santa left?
- Key: Business Card
iv.
Question 4
- In 2016, Linux terminals at the North Pole
could be accessed with what kind of computer?
- Key: Cranberry Pi
v.
Question 5
- In 2017, the North Pole was being
bombarded by giant objects. What were they?
- Key: Snowballs
vi.
Question 6
- In 2017, Sam the snowman needed help
reassembling pages torn from what?
- Key: The Great Book
c.


d.
Sub Challenge:
i.
Challenge: leave the vi text editor screen
- Key: ":q!"
ii.
Steps:
- On the Essential Editor Skills Cranberry
Pi:
- Opening the Cranberry Pi puts you in a
test message.
- Enter command below to get out of the text
editor
a.
:q!
b.


c.


2.
Directory Browsing
a.
Challenge
Difficulty: 1/5
Who submitted (First Last) the
rejected talk titled Data Loss for Rainbow Teams: A Path in the Darkness? Please analyze the CFP site to find out. For hints on achieving this objective, please
visit Minty Candycane and help her with the The Name Game Cranberry
Pi terminal challenge.
i.
Key: John Mclane
b.
Steps
c.


d.
![alidating data store for employee onboard information .
Enter address of server: & "sq1ite3"
sage: ping [-aAbBdDfhLnOqrRUvV] [-c count] [ -i interval] [-1 interface]
[ -m mark] [ -M pmtudisc_option] [-1 preload] [-p pattern] [-Q tos]
[ -s packetsize] [ -S sndbuf] [-t ttl] [ -T timestamp_option]
[ -w deadline] [ -W timeout] [hopl . ] destination
•te version 3.11.ø 2816-82-15
Enter " .help" for usage hints.
ected to a transient in-mermry database.
se " .open FILENAME" to reopen on a persistent database.
qlite>
. bash logout . cache/
. bashrc
. local/
. profile
menu . PSI
onboard. db
runtoanswer
qlite> .open onboard. db
qlite> . tables
board
qlite> .dump onboard
foreign_keys —OFF ;
N TRANSACTION;
TE TABLE onboard (
id INTEGER PRIMARY KEY,
fname TEXT WLL,
Iname TEXT WLL,
streetl TEXT,
street2 TEXT,
city TEXT,
postalcode TEXT,
phone TEXT,
email TEXT
NSERT INTO "onboard" VALUES(IØ, 'Karen' , 'Duck' , '52 Annfield Rd' ,NULL, 'BEAL' , 'DN14 7AU', '877 8656 6
, • karensduck*inrot.com• ) ;
NSERT INTO "onboard" VALUES(II, •Josephine • , •Harrell , • 3 Victoria Road • ,
• , •879 5532 7917 • , josephinedharrell@einrot.com •
NSERT INTO "onboard" VALUES(12, 'Jason' , •madsen• , '4931 Cliffside Drive' ,
NSERT INTO "onboard" VALUES(13, •Nichole' , •murphy• , • 53 St. John Street • ,
-734-9891 • , •nicholenmurphy@teleworm.us • ) ;
WLL, 'LITTLE ASTON', '874 8
WLL, •Worcester • , 12197 • , '
WLL, •craik', •s4P 3Y2',
NSERT INTO "onboard" VALUES(14, •mary•, 'Lyons', '569 York Mills Rd' ,NULL, 'Toronto', •,'43B 1','2', '416-2
4-6639' , •maryjlyons@superrito.com• ) ;
NSERT INTO "onboard" VALUES(15, 'Luz' , •west' , '13e7 Poe Lane' *NULL, 'Paola' , '66071' ,
uzcwest@rhyta.cun • ) ;
NSERT INTO "onboard" VALUES(16, •walter• , , '4782 Neville street • ,WLL, •seymour• , '47274' , '81](file:///C:/Users/chris/AppData/Local/Temp/msohtmlclip1/01/clip_image010.jpg)
![alidating data store for employee onboard information .
Enter address of server: & "sq1ite3"
sage: ping [-aAbBdDfhLnOqrRUvV] [-c count] [ -i interval] [-1 interface]
[ -m mark] [ -M pmtudisc_option] [-1 preload] [-p pattern] [-Q tos]
[ -s packetsize] [ -S sndbuf] [-t ttl] [ -T timestamp_option]
[ -w deadline] [ -W timeout] [hopl . ] destination
•te version 3.11.ø 2816-82-15
Enter " .help" for usage hints.
ected to a transient in-mermry database.
se " .open FILENAME" to reopen on a persistent database.
qlite>
. bash logout . cache/
. bashrc
. local/
. profile
menu . PSI
onboard. db
runtoanswer
qlite> .open onboard. db
qlite> . tables
board
qlite> .dump onboard
foreign_keys —OFF ;
N TRANSACTION;
TE TABLE onboard (
id INTEGER PRIMARY KEY,
fname TEXT WLL,
Iname TEXT WLL,
streetl TEXT,
street2 TEXT,
city TEXT,
postalcode TEXT,
phone TEXT,
email TEXT
NSERT INTO "onboard" VALUES(IØ, 'Karen' , 'Duck' , '52 Annfield Rd' ,NULL, 'BEAL' , 'DN14 7AU', '877 8656 6
, • karensduck*inrot.com• ) ;
NSERT INTO "onboard" VALUES(II, •Josephine • , •Harrell , • 3 Victoria Road • ,
• , •879 5532 7917 • , josephinedharrell@einrot.com •
NSERT INTO "onboard" VALUES(12, 'Jason' , •madsen• , '4931 Cliffside Drive' ,
NSERT INTO "onboard" VALUES(13, •Nichole' , •murphy• , • 53 St. John Street • ,
-734-9891 • , •nicholenmurphy@teleworm.us • ) ;
WLL, 'LITTLE ASTON', '874 8
WLL, •Worcester • , 12197 • , '
WLL, •craik', •s4P 3Y2',
NSERT INTO "onboard" VALUES(14, •mary•, 'Lyons', '569 York Mills Rd' ,NULL, 'Toronto', •,'43B 1','2', '416-2
4-6639' , •maryjlyons@superrito.com• ) ;
NSERT INTO "onboard" VALUES(15, 'Luz' , •west' , '13e7 Poe Lane' *NULL, 'Paola' , '66071' ,
uzcwest@rhyta.cun • ) ;
NSERT INTO "onboard" VALUES(16, •walter• , , '4782 Neville street • ,WLL, •seymour• , '47274' , '81](file:///C:/Users/chris/AppData/Local/Temp/msohtmlclip1/01/clip_image010.jpg)
e.
.she
f.


g.


h.


i.


j.


k.


l.


m.


n.


3.
de Bruijn Sequences
a.
The Challenge
i.
When you break into the speaker unpreparedness
room, what does Morcel Nougat say? For hints on achieving this objective,
please visit Tangle Coalbox and help him with Lethal ForensicELFication
Cranberry Pi terminal challenge.
ii.
Key: Welcome unprepared
speaker!
b.
Steps
i.
K=4 n=4
1.
Table of possibilities:
a.
0
0 0 0 1
0 0 0 2
0 0 0 3
0 0 1 1
0 0 1 2
0 0 1 3
0 0 2 1
0 0 2 2
0 0 2 3
0 0 3 1
0 0 3 2
0 0 3 3
0 1
0 1 0 2
0 1 0 3
0 1 1 1
0 1 1 2
0 1 1 3
0 1 2 1
0 1 2 2
0 1 2 3
0 1 3 1
0 1 3 2
0 1 3 3
0 2
0 2 0 3
0 2 1 1
0 2 1 2
0 2 1 3
0 2 2 1
0 2 2 2
0 2 2 3
0 2 3 1
0 2 3 2
0 2 3 3
0 3
0 3 1 1
0 3 1 2
0 3 1 3
0 3 2 1
0 3 2 2
0 3 2 3
0 3 3 1
0 3 3 2
0 3 3 3
1
1 1 1 2
1 1 1 3
1 1 2 2
1 1 2 3
1 1 3 2
1 1 3 3
1 2
1 2 1 3
1 2 2 2
1 2 2 3
1 2 3 2
1 2 3 3
1 3
1 3 2 2
1 3 2 3
1 3 3 2
1 3 3 3
2
2 2 2 3
2 2 3 3
2 3
2 3 3 3
3
0 0 0 1
0 0 0 2
0 0 0 3
0 0 1 1
0 0 1 2
0 0 1 3
0 0 2 1
0 0 2 2
0 0 2 3
0 0 3 1
0 0 3 2
0 0 3 3
0 1
0 1 0 2
0 1 0 3
0 1 1 1
0 1 1 2
0 1 1 3
0 1 2 1
0 1 2 2
0 1 2 3
0 1 3 1
0 1 3 2
0 1 3 3
0 2
0 2 0 3
0 2 1 1
0 2 1 2
0 2 1 3
0 2 2 1
0 2 2 2
0 2 2 3
0 2 3 1
0 2 3 2
0 2 3 3
0 3
0 3 1 1
0 3 1 2
0 3 1 3
0 3 2 1
0 3 2 2
0 3 2 3
0 3 3 1
0 3 3 2
0 3 3 3
1
1 1 1 2
1 1 1 3
1 1 2 2
1 1 2 3
1 1 3 2
1 1 3 3
1 2
1 2 1 3
1 2 2 2
1 2 2 3
1 2 3 2
1 2 3 3
1 3
1 3 2 2
1 3 2 3
1 3 3 2
1 3 3 3
2
2 2 2 3
2 2 3 3
2 3
2 3 3 3
3
![Activities 9 Google Chrome
Holiday Hack Cha x
Forensic Relevance
Tue Jan 1, 11:45
Work - Microsoft C;
de Bruijn (deBruijn)
x
x
• Secure https://kringlecon.com/?modal=challenge&rid=00e0a60a-f586-4a1
: Apps Tech Sites O AVHE O ITC LABS AVHE-Calendar a
Swift GDS Query Scre Wheel Decide l! //
timesheet
Enter the Code to Unlockthe Door
O)) [i] 550/0 v
Christopher
ABP
Other bookmarks
ForensicEl
New [Narrative] Unlocked: !
Click here to see this item in yo
New [Narrative] Unlocked: !
Click here to see this item in yo
New [Achievement] Unlock(
Click here to see this item in your badge:
AOOA
Correct guess!
Close
equence
1:22PM
e page source, but found nothing
Imost all the challenges except this one
passcode? Speaker UNpreparedness
ning a Ford Lock Code video
- the webpage
'I
January 1st
Ite forcing thing, for the room code? 4!
e something more efficient and fun?
/badges
Hellooo! Type here to chat.](file:///C:/Users/chris/AppData/Local/Temp/msohtmlclip1/01/clip_image030.png)
![Activities 9 Google Chrome
Holiday Hack Cha x
Forensic Relevance
• Secure https://kringlecon.com
: Apps Tech Sites O AVHE O ITC LABS
Work - Microsoft C;
x
Swift
Calendar a
AVHE -
Tue Jan 1, 11:46
de Bruijn (deBruijn)
x
GDS Query Scre Wheel Decide I !
O)) [i] 550/0 v
Christopher
ABP
Other bookmarks
timesheet
Current Area: 13
lightning342 10:25AM
Marcel is not very chatty :(
keyboardkrackers 1:29PM
Hello @Morcel
WHY AR U NOT TALKING!!!!
tinkerbell
jwsec
Welcome unprepared speaker!
Welcome unprepared speaker!
Morcel Nougat hammythehammer
Hellooo! Type here to chat.
O
Hello @Morcel hello Morcel Nouget Hello @Morcel Hello
Morcel hi *morcel
hello morcel
oh! i get it now....
dootyfree 2:55PM
Hello
slammajamma 8:09PM
Hello @Morcel
lowfidelityioc 8:09PM
Hello @Morcel
ponydanza 10:40PM
hello @Morcel
Hello Morcel
Hello @Morcel
hi *morcel
January 1st
infamousbkny 7:12AM
Hello @Morcel
onty 8:47AM
Hello @Morcel](file:///C:/Users/chris/AppData/Local/Temp/msohtmlclip1/01/clip_image032.png)
c.
Sub-Challenge at Tangle Coalbox "Lethal
ForensicELFFication
1.
Christmas is coming, and so it would seem,
ER (Elf Resources) crushes elves' dreams.
One tells me she was disturbed by a bloke.
He tells me this must be some kind of joke.
Please do your best to determine what's real.
Has this jamoke, for this elf, got some feels?
Lethal forensics ain't my cup of tea;
If YOU can fake it, my hero you'll be.
One more quick note that might help you complete,
Clearing this mess up that's now at your feet.
Certain text editors can leave some clue.
Did our young Romeo leave one for you?
- Tangle Coalbox, ER Investigator
Find the first name of the elf of whom a love poem
was written. Complete this challenge by submitting
that name to runtoanswer.
ER (Elf Resources) crushes elves' dreams.
One tells me she was disturbed by a bloke.
He tells me this must be some kind of joke.
Please do your best to determine what's real.
Has this jamoke, for this elf, got some feels?
Lethal forensics ain't my cup of tea;
If YOU can fake it, my hero you'll be.
One more quick note that might help you complete,
Clearing this mess up that's now at your feet.
Certain text editors can leave some clue.
Did our young Romeo leave one for you?
- Tangle Coalbox, ER Investigator
Find the first name of the elf of whom a love poem
was written. Complete this challenge by submitting
that name to runtoanswer.
2.
Key: Elinore
1. The
Steps
- Check the directory
![Activities 9 Google Chrome
Holiday Hack Cha x
Forensic Relevance
Tue Jan
Work - Microsoft C;
x
1, 11:24
• Secure https://kringlecon.com/?modal=challenge&rid=92946c88-50e1-49e2-a8d1-ab106a0cf1 d6&challenge=viminfo
: Apps Tech Sites O AVHE O ITC LABS AVHE-Calendar a
Swift GDS Query Scre Wheel Decide l! //
timesheet
•e O)) [i] 64% v
Christopher
ABP
Other bookmarks
Find the first name of the
was written.
Complete thi
that name to runtoanswer
elf@02b2342b90e7 : -$
elf@02b2342b90e7 : -$
elf@02b2342b90e7 : -$
runtoanswer
-al
elf of whom a love poem
halleng
ebysubmitting
total 5460
drwxr-xr-x 1
drwxr-xr-x 1
- rw- r-
- rw- r-
- rw- r-
- rw- r-
drwxr-xr-x 1
- rw- r-
- rwxr-xr-x 1
root
root
4096
4096
419
220
3540
675
4096
5063
elf 5551072
Dec
Dec
Dec
May
Dec
May
Dec
Dec
Dec
14
14
14
15
14
15
14
14
14
16:28
16:28
16:13
2017
16:28
2017
16:28
16:13
16:13
. bash history
. bash logout
. bashrc
. profile
. secrets
. viminfo
runtoanswer
elf@02b2342b90e7.-
• $ cat . / . secrets/
Is a directory
M. secrets/ :
cat :
elf@02b2342b90e7 : -
$ Is -al ./.secrets/her/poem.txt
. bash history
. bashrc
. secrets/
runtoanswer
. bash logout
. profile
. viminfo
Is -al . / . secrets/her/poem. txt
1 elf elf 1880 Dec 14 16:13 ./.secrets/her/poem.txt
- rw- r-
cat . / . secrets/her/poem. txt
Once upon a sleigh so weary, Morcel scrubbed the grime so dreary,
Shining many a beautiful sleighbell bearing cheer and sound so pure--
There he cleaned them, nearly napping, suddenly there came a tapping,
s of someone gently rapping, rapping at the sleigh house door.
IT is some caroler,
he muttered,
"tapping at my sleigh house door--
Only this and nothing more.
hen, continued with more vigor, came the sound he didn't figure,
Close
Hellooo! Type here to chat.
equence
1:22PM
e page source, but found nothing
Imost all the challenges except this one
passcode? Speaker UNpreparedness
ning a Ford Lock Code video
- the webpage
'I
January 1st
Ite forcing thing, for the room code? 4!
e something more efficient and fun?
/badges](file:///C:/Users/chris/AppData/Local/Temp/msohtmlclip1/01/clip_image034.png)
2.
elf@02b2342b90e7:~$ cat ./.viminfo
a.
# This viminfo file was generated by
Vim 8.0.
# You may edit it if you're careful!
# Viminfo version
|1,4
# Value of 'encoding' when this file was written
*encoding=utf-8
# hlsearch on (H) or off (h):
~h
# Last Substitute Search Pattern:
~MSle0~&Elinore
# Last Substitute String:
$NEVERMORE
# You may edit it if you're careful!
# Viminfo version
|1,4
# Value of 'encoding' when this file was written
*encoding=utf-8
# hlsearch on (H) or off (h):
~h
# Last Substitute Search Pattern:
~MSle0~&Elinore
# Last Substitute String:
$NEVERMORE
3.
# Command Line History (newest to
oldest):
:wq
|2,0,1536607231,,"wq"
:%s/Elinore/NEVERMORE/g
|2,0,1536607217,,"%s/Elinore/NEVERMORE/g"
:r .secrets/her/poem.txt
|2,0,1536607201,,"r .secrets/her/poem.txt"
:q
|2,0,1536606844,,"q"
:w
|2,0,1536606841,,"w"
:s/God/fates/gc
|2,0,1536606833,,"s/God/fates/gc"
:%s/studied/looking/g
|2,0,1536602549,,"%s/studied/looking/g"
:%s/sound/tenor/g
|2,0,1536600579,,"%s/sound/tenor/g"
:r .secrets/her/poem.txt
|2,0,1536600314,,"r .secrets/her/poem.txt"
# Search String History (newest to oldest):
:wq
|2,0,1536607231,,"wq"
:%s/Elinore/NEVERMORE/g
|2,0,1536607217,,"%s/Elinore/NEVERMORE/g"
:r .secrets/her/poem.txt
|2,0,1536607201,,"r .secrets/her/poem.txt"
:q
|2,0,1536606844,,"q"
:w
|2,0,1536606841,,"w"
:s/God/fates/gc
|2,0,1536606833,,"s/God/fates/gc"
:%s/studied/looking/g
|2,0,1536602549,,"%s/studied/looking/g"
:%s/sound/tenor/g
|2,0,1536600579,,"%s/sound/tenor/g"
:r .secrets/her/poem.txt
|2,0,1536600314,,"r .secrets/her/poem.txt"
# Search String History (newest to oldest):
4.
? Elinore
|2,1,1536607217,,"Elinore"
? God
|2,1,1536606833,,"God"
? rousted
|2,1,1536605996,,"rousted"
? While
|2,1,1536604909,,"While"
? studied
|2,1,1536602549,,"studied"
? sound
|2,1,1536600579,,"sound"
# Expression History (newest to oldest):
# Input Line History (newest to oldest):
# Debug Line History (newest to oldest):
# Registers:
"1 LINE 0
|3,0,1,1,1,0,1536605034,""
""- CHAR 0
.
|3,1,36,0,1,0,1536606803,"."
# File marks:
'0 34 2 ~/.secrets/her/poem.txt
|4,48,34,2,1536607231,"~/.secrets/her/poem.txt"
'1 24 0 ~/.secrets/her/poem.txt
|4,49,24,0,1536606844,"~/.secrets/her/poem.txt"
'2 24 0 ~/.secrets/her/poem.txt
|4,50,24,0,1536606844,"~/.secrets/her/poem.txt"
|2,1,1536607217,,"Elinore"
? God
|2,1,1536606833,,"God"
? rousted
|2,1,1536605996,,"rousted"
? While
|2,1,1536604909,,"While"
? studied
|2,1,1536602549,,"studied"
? sound
|2,1,1536600579,,"sound"
# Expression History (newest to oldest):
# Input Line History (newest to oldest):
# Debug Line History (newest to oldest):
# Registers:
"1 LINE 0
|3,0,1,1,1,0,1536605034,""
""- CHAR 0
.
|3,1,36,0,1,0,1536606803,"."
# File marks:
'0 34 2 ~/.secrets/her/poem.txt
|4,48,34,2,1536607231,"~/.secrets/her/poem.txt"
'1 24 0 ~/.secrets/her/poem.txt
|4,49,24,0,1536606844,"~/.secrets/her/poem.txt"
'2 24 0 ~/.secrets/her/poem.txt
|4,50,24,0,1536606844,"~/.secrets/her/poem.txt"
5.
'2
24 0 ~/.secrets/her/poem.txt
|4,50,24,0,1536606844,"~/.secrets/her/poem.txt"
'3 37 0 ~/.secrets/her/poem.txt
|4,51,37,0,1536606647,"~/.secrets/her/poem.txt"
'4 37 0 ~/.secrets/her/poem.txt
|4,52,37,0,1536606647,"~/.secrets/her/poem.txt"
'5 37 0 ~/.secrets/her/poem.txt
|4,53,37,0,1536606647,"~/.secrets/her/poem.txt"
'6 37 0 ~/.secrets/her/poem.txt
|4,54,37,0,1536606647,"~/.secrets/her/poem.txt"
'7 22 0 ~/.secrets/her/poem.txt
|4,55,22,0,1536602320,"~/.secrets/her/poem.txt"
'8 22 0 ~/.secrets/her/poem.txt
|4,56,22,0,1536602320,"~/.secrets/her/poem.txt"
'9 22 0 ~/.secrets/her/poem.txt
|4,57,22,0,1536602320,"~/.secrets/her/poem.txt"
# Jumplist (newest first):
-' 34 2 ~/.secrets/her/poem.txt
|4,39,34,2,1536607231,"~/.secrets/her/poem.txt"
-' 24 0 ~/.secrets/her/poem.txt
|4,39,24,0,1536607217,"~/.secrets/her/poem.txt"
-' 24 0 ~/.secrets/her/poem.txt
|4,39,24,0,1536606844,"~/.secrets/her/poem.txt"
-' 37 0 ~/.secrets/her/poem.txt
|4,39,37,0,1536606752,"~/.secrets/her/poem.txt"
-' 37 0 ~/.secrets/her/poem.txt
|4,39,37,0,1536606752,"~/.secrets/her/poem.txt"
-' 37 0 ~/.secrets/her/poem.txt
|4,39,37,0,1536606647,"~/.secrets/her/poem.txt"
-' 31 56 ~/.secrets/her/poem.txt
|4,39,31,56,1536605996,"~/.secrets/her/poem.txt"
-' 31 56 ~/.secrets/her/poem.txt
|4,39,31,56,1536605996,"~/.secrets/her/poem.txt"
-' 31 56 ~/.secrets/her/poem.txt
|4,39,31,56,1536605996,"~/.secrets/her/poem.txt"
|4,50,24,0,1536606844,"~/.secrets/her/poem.txt"
'3 37 0 ~/.secrets/her/poem.txt
|4,51,37,0,1536606647,"~/.secrets/her/poem.txt"
'4 37 0 ~/.secrets/her/poem.txt
|4,52,37,0,1536606647,"~/.secrets/her/poem.txt"
'5 37 0 ~/.secrets/her/poem.txt
|4,53,37,0,1536606647,"~/.secrets/her/poem.txt"
'6 37 0 ~/.secrets/her/poem.txt
|4,54,37,0,1536606647,"~/.secrets/her/poem.txt"
'7 22 0 ~/.secrets/her/poem.txt
|4,55,22,0,1536602320,"~/.secrets/her/poem.txt"
'8 22 0 ~/.secrets/her/poem.txt
|4,56,22,0,1536602320,"~/.secrets/her/poem.txt"
'9 22 0 ~/.secrets/her/poem.txt
|4,57,22,0,1536602320,"~/.secrets/her/poem.txt"
# Jumplist (newest first):
-' 34 2 ~/.secrets/her/poem.txt
|4,39,34,2,1536607231,"~/.secrets/her/poem.txt"
-' 24 0 ~/.secrets/her/poem.txt
|4,39,24,0,1536607217,"~/.secrets/her/poem.txt"
-' 24 0 ~/.secrets/her/poem.txt
|4,39,24,0,1536606844,"~/.secrets/her/poem.txt"
-' 37 0 ~/.secrets/her/poem.txt
|4,39,37,0,1536606752,"~/.secrets/her/poem.txt"
-' 37 0 ~/.secrets/her/poem.txt
|4,39,37,0,1536606752,"~/.secrets/her/poem.txt"
-' 37 0 ~/.secrets/her/poem.txt
|4,39,37,0,1536606647,"~/.secrets/her/poem.txt"
-' 31 56 ~/.secrets/her/poem.txt
|4,39,31,56,1536605996,"~/.secrets/her/poem.txt"
-' 31 56 ~/.secrets/her/poem.txt
|4,39,31,56,1536605996,"~/.secrets/her/poem.txt"
-' 31 56 ~/.secrets/her/poem.txt
|4,39,31,56,1536605996,"~/.secrets/her/poem.txt"
6.
elf@02b2342b90e7:~$ cat
./.secrets/her/poem.txt
a.
Once upon a sleigh so weary, Morcel
scrubbed the grime so dreary,
Shining many a beautiful sleighbell bearing cheer and sound so pure--
There he cleaned them, nearly napping, suddenly there came a tapping,
As of someone gently rapping, rapping at the sleigh house door.
"'Tis some caroler," he muttered, "tapping at my sleigh house door--
Only this and nothing more."
Then, continued with more vigor, came the sound he didn't figure,
Could belong to one so lovely, walking 'bout the North Pole grounds.
But the truth is, she WAS knocking, 'cause with him she would be talking,
Off with fingers interlocking, strolling out with love newfound?
Gazing into eyes so deeply, caring not who sees their rounds.
Oh, 'twould make his heart resound!
Hurried, he, to greet the maiden, dropping rag and brush - unlaiden.
Floating over, more than walking, moving toward the sound still knocking,
Pausing at the elf-length mirror, checked himself to study clearer,
Fixing hair and looking nearer, what a hunky elf - not shocking!
Peering through the peephole smiling, reaching forward and unlocking:
NEVERMORE in tinsel stocking! Greeting her with smile dashing, pearly-white incisors flashing,
Telling jokes to keep her laughing, soaring high upon the tidings,
Of good fortune fates had borne him. Offered her his dexter forelimb,
Never was his future less dim! Should he now consider gliding--
No - they shouldn't but consider taking flight in sleigh and riding
Up above the Pole abiding?
Smile, she did, when he suggested that their future surely rested,
llenUp in flight above their cohort flying high like ne'er before!
So he harnessed two young reindeer, bold and fresh and bearing no fear.
In they jumped and seated so near, off they flew - broke through the door!
Up and up climbed team and humor, Morcel being so adored,
By his lovely NEVERMORE!
-Morcel Nougat
Shining many a beautiful sleighbell bearing cheer and sound so pure--
There he cleaned them, nearly napping, suddenly there came a tapping,
As of someone gently rapping, rapping at the sleigh house door.
"'Tis some caroler," he muttered, "tapping at my sleigh house door--
Only this and nothing more."
Then, continued with more vigor, came the sound he didn't figure,
Could belong to one so lovely, walking 'bout the North Pole grounds.
But the truth is, she WAS knocking, 'cause with him she would be talking,
Off with fingers interlocking, strolling out with love newfound?
Gazing into eyes so deeply, caring not who sees their rounds.
Oh, 'twould make his heart resound!
Hurried, he, to greet the maiden, dropping rag and brush - unlaiden.
Floating over, more than walking, moving toward the sound still knocking,
Pausing at the elf-length mirror, checked himself to study clearer,
Fixing hair and looking nearer, what a hunky elf - not shocking!
Peering through the peephole smiling, reaching forward and unlocking:
NEVERMORE in tinsel stocking! Greeting her with smile dashing, pearly-white incisors flashing,
Telling jokes to keep her laughing, soaring high upon the tidings,
Of good fortune fates had borne him. Offered her his dexter forelimb,
Never was his future less dim! Should he now consider gliding--
No - they shouldn't but consider taking flight in sleigh and riding
Up above the Pole abiding?
Smile, she did, when he suggested that their future surely rested,
llenUp in flight above their cohort flying high like ne'er before!
So he harnessed two young reindeer, bold and fresh and bearing no fear.
In they jumped and seated so near, off they flew - broke through the door!
Up and up climbed team and humor, Morcel being so adored,
By his lovely NEVERMORE!
-Morcel Nougat
7.
./runtoanswer … Elinore
a.


4.
Data Repo Analysis
a.
The Challenge:
i.
Retrieve the encrypted ZIP file from
the North Pole Git repository. What is the password to open this file? For hints on
achieving this objective, please visit Wunorse Openslae and help him with Stall
Mucking Report Cranberry Pi terminal challenge.
1.
Key: Yippee-ki-yay
ii.
Steps:
iii.
Locally installed pip
1.
Sudo apt install python3-pip
iv.
Locally installed truffleHog
1.
Sudo pip3 install truffleHog
v.
Ran truffleHog with entropy as TRUE
against the git site
1.

b.
SubChallenge:
i. The Challenge:
Thank you Madam or Sir for the help that you bring!
I was wondering how I might rescue my day.
Finished mucking out stalls of those pulling the sleigh,
My report is now due or my KRINGLE's in a sling!
There's a samba share here on this terminal screen.
What I normally do is to upload the file,
With our network credentials (we've shared for a while).
When I try to remember, my memory's clean!
Be it last night's nog bender or just lack of rest,
For the life of me I can't send in my report.
Could there be buried hints or some way to contort,
Gaining access - oh please now do give it your best!
-Wunorse Openslae
Complete this challenge by uploading the elf's report.txt
file to the samba share at //localhost/report-upload/
ii. The Key: smbclient //localhost/report-upload/
directreindeerflatterystable -U report-upload -c 'put "report.txt"'
iii. Steps:
- elf@f44cb9cdbfae:~$ ps af
>> text.txt
elf@f44cb9cdbfae:~$
cat ./text.txt
PID TTY
STAT TIME COMMAND
1 pts/0
Ss 0:00 /bin/bash /sbin/init
11 pts/0
S 0:00 sudo -u manager
/home/manager/samba-wrapper.sh --verbosity=none --no-check-certificate
--extraneous-command-argument --do-not-run-as-tyler --accept-sage-advice -a 42
-d~ --ignore-sw-holiday-special --suppress --suppress
//localhost/report-upload/ directreindeerflatterystable -U report-upload
19 pts/0
S 0:00 \_ /bin/bash /home/manager/samba-wrapper.sh
--verbosity=none --no-check-certificate --extraneous-command-argument
--do-not-run-as-tyler --accept-sage-advice -a 42 -d~
--ignore-sw-holiday-special --suppress --suppress //localhost/report-upload/ directreindeerflatterystable
-U report-upload
22 pts/0
S 0:00 \_ sleep 60
12 pts/0
S 0:00 sudo -E -u manager
/usr/bin/python /home/manager/report-check.py
17 pts/0
S 0:00 \_ /usr/bin/python
/home/manager/report-check.py
16 pts/0
S 0:00 sudo -u elf /bin/bash
18 pts/0
S 0:00 \_ /bin/bash
33 pts/0 R+
0:00 \_ ps af
2.
Used credentials to craft smbclient
command to upload the report:
a.
smbclient //localhost/report-upload/
directreindeerflatterystable -U report-upload -c 'put "report.txt"'
![Activities
Google Chrome
Holiday x
Password x
Work - Ml
x
.cc::::
shell-Ho x
Tue Jan 1, 19:35
shell- x An A-Z Irv x
fi 100% v
Sending f x
linux-Vi€
x
Linux
x
Secure https://kringlecon.com/?modal=challenge&rid=34ebc244-ea0e-406c-8863-0c8b01
: Apps Tech Sites O AVHE O ITC LABS AVHE-Calendar
Swift GDS Query Scre Wheel Decide l! //
timesheet
a
report . txt
elf@fed4e6393a40:—$ smbclient // local host/ report-upload/ direct reindeer flatterystable
eport-upload -c I put " report. txt"
ARNING: The "sys log" option is deprecated
Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.5.12 -Debian]
putting file report. txt as \ report. txt (250.5 kb/s) (average 250.5 kb/s)
elf@fed4e6393a40 : -$
Christopher
ABP
Other bookmarks
, NWOkkkkkkkkkkkkkkNN ;
.. KM; Stall Mucking , MN.
OMNXNMd .
.0MWXXMO .
: MO
: MO
0MO
IONNNNNNNNNNNNNNNOo
dOOOOOOOOOOOOOOOOOd .
. ONNNNNNNNNNNNNNNNNO .
. MMMMMMMMMMMMMM ,
. ONNNNNNNNXk
dOOOOOOOOOo
CCCCCCCCCCCCCC:
. WMMMMMMMMMMMMMMMW.
xMc
xMd ,
„„clll:.
' kkkkxxxxxddddddoooooooxM0
' kkkkxxxxxddddddoooooooxM0
' kkkkxxxxxddddddoooooooxM0
: MO
: MO
: MO
: MO
: MO
. NWxddddddddddddddddddddddddNW
; ccccccccccccccccccccccccc ;
You have found the credentials I just had forgot,
nd in doing so you've saved me trouble untold.
Going forward we Ill leave behind policies old,
Building separate accounts for each elf in the lot.
Close
Hellooo! Type here to chat.
the zip file burried in the repository.
it.
assword
le a pointer on where to get started with
sword for Wunrose? Tried looking at Cron
ICk.
Inks (assuming that was in reply to my
says resource not available when I
@ian1535
try without the password](file:///C:/Users/chris/AppData/Local/Temp/msohtmlclip1/01/clip_image040.png)
5.
AD Privilege Discovery
a.
The Challenge
i.
Using the data set contained in this SANS Slingshot Linux image,
find a reliable path from a Kerberoastable user to the Domain Admins group.
What’s the user’s logon name? Remember to avoid RDP as a control path as it
depends on separate local privilege escalation flaws. For hints on achieving
this objective, please visit Holly Evergreen and help her with the CURLing
Master Cranberry Pi terminal challenge.
1.
Key: LDUBEJ00320@AD.KRINGLECASTLE.COM
ii.
Steps
1.
Downloaded HHC2018-DomainHack_2018-12-19.ova to
local machine
2.
Imported and started within Workstation pro
3.
From VM desktop, launched pre-loaded
"bloodhound' session
a.


4.
Looked for path from Kerberoastable to Domain
Admins group, making sure not to traverse an "CanRDP" path; simply
using session/token data
a.


5.
Looked at root user path's data and found user
logon name
a.


6.
Imported full name into challenge question: LDUBEJ00320@AD.KRINGLECASTLE.COM
b.
Sub Challenge
i.
I am Holly Evergreen, and now you won't believe:
Once again the striper stopped; I think I might just leave!
Bushy set it up to start upon a website call.
Darned if I can CURL it on - my Linux skills apall.
Could you be our CURLing master - fixing up this mess?
If you are, there's one concern you surely must address.
Something's off about the conf that Bushy put in place.
Can you overcome this snag and save us all some face?
Complete this challenge by submitting the right HTTP
request to the server at http://localhost:8080/ to
get the candy striper started again. You may view
the contents of the nginx.conf file in
/etc/nginx/, if helpful.
Once again the striper stopped; I think I might just leave!
Bushy set it up to start upon a website call.
Darned if I can CURL it on - my Linux skills apall.
Could you be our CURLing master - fixing up this mess?
If you are, there's one concern you surely must address.
Something's off about the conf that Bushy put in place.
Can you overcome this snag and save us all some face?
Complete this challenge by submitting the right HTTP
request to the server at http://localhost:8080/ to
get the candy striper started again. You may view
the contents of the nginx.conf file in
/etc/nginx/, if helpful.
iii.
Steps:
1.
Checked out /etc/conf/nginx.conf
server {
# love using the new stuff! -Bushy
listen 8080 http2;
# server_name localhost 127.0.0.1;
root /var/www/html;
location ~ [^/]\.php(/|$) {
fastcgi_split_path_info ^(.+?\.php)(/.*)$;
if (!-f $document_root$fastcgi_script_name) {
return 404;
}
# Mitigate https://httpoxy.org/ vulnerabilities
fastcgi_param HTTP_PROXY "";
# fastcgi_pass 127.0.0.1:9000;
fastcgi_pass unix:/var/run/php/php-fpm.sock;
fastcgi_index index.php;
# include the fastcgi_param setting
include fastcgi_params;
# SCRIPT_FILENAME parameter is used for PHP FPM determining
# the script name. If it is not set in fastcgi_params file,
# i.e. /etc/nginx/fastcgi_params or in the parent contexts,
# please comment off following line:
# fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
}
# love using the new stuff! -Bushy
listen 8080 http2;
# server_name localhost 127.0.0.1;
root /var/www/html;
location ~ [^/]\.php(/|$) {
fastcgi_split_path_info ^(.+?\.php)(/.*)$;
if (!-f $document_root$fastcgi_script_name) {
return 404;
}
# Mitigate https://httpoxy.org/ vulnerabilities
fastcgi_param HTTP_PROXY "";
# fastcgi_pass 127.0.0.1:9000;
fastcgi_pass unix:/var/run/php/php-fpm.sock;
fastcgi_index index.php;
# include the fastcgi_param setting
include fastcgi_params;
# SCRIPT_FILENAME parameter is used for PHP FPM determining
# the script name. If it is not set in fastcgi_params file,
# i.e. /etc/nginx/fastcgi_params or in the parent contexts,
# please comment off following line:
# fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
}
2.
Checked into index.php

a.
Errored out still
6.
Badge Manipulation
a.
Challenge:
i.
Bypass the authentication mechanism associated
with the room near Pepper Minstix. A sample employee badge is available. What
is the access control number revealed by the door authentication panel? For
hints on achieving this objective, please visit Pepper Minstix and help her
with the Yule Log Analysis Cranberry Pi terminal challenge.
ii.
Key: 19880715
iii.
Steps:
1.
Utilize this site to generate QR
codes from text input: https://www.the-qrcode-generator.com/
a.


2.
Generated bad code which yielded
proper SQL syntax
a.
"USER_INFO = QUERY("SELECT
FIRST_NAME,LAST_NAME,ENABLED FROM EMPLOYEES WHERE AUTHORIZED = 1 AND UID = '{}'
LIMIT 1".FORMAT(UID))"): (C1064, u"
3.
Created RQ code for sql injection bypass: or 1--
-' or 1 or '1"or 1 or"
a.
Showed that entry user must be ENABLED and
AUTHORISED
4.
Because uid is not required put OR operator in
and created section to look for enabled users, commented out limit
a.
'or enabled = 1 #
i.
The single quote ends the UID = search
ii.
AND performs and operation of either UID or
enabled
iii.
Enabled = 1 follows the same syntax for
authorized = 1
iv.
# comments out the limit = 1 and the rest of the
sql command
b.


c.
Answer is: 19880715
b.
Sub Challenge:
i.
Challenge:
I am
Pepper Minstix, and I'm looking for your help.
Bad guys have us tangled up in pepperminty kelp!
"Password spraying" is to blame for this our grinchly fate.
Should we blame our password policies which users hate?
Bad guys have us tangled up in pepperminty kelp!
"Password spraying" is to blame for this our grinchly fate.
Should we blame our password policies which users hate?
Here
you'll find a web log filled with failure and success.
One successful login there requires your redress.
Can you help us figure out which user was attacked?
Tell us who fell victim, and please handle this with tact...
One successful login there requires your redress.
Can you help us figure out which user was attacked?
Tell us who fell victim, and please handle this with tact...
Submit
the compromised webmail username to
runtoanswer to complete this challenge.
runtoanswer to complete this challenge.
Key:
minty.candycane
ii.
Steps:
1.
From Cranberry Pi Terminal, ran the
following command to dump the windows event file into a csv from ho-ho0ho.evtx,
grep on "UserName" and "EventData", sort to only show the
unique strings
2.


3.
Since the username list was a short
stack, Input of usernames one by one was best method for runtoanswer script
4.
Ran ./runtoanswer

7.
Some
a.
Challenge
b.
Sub challenge
i.
The challenge
1.
Coalbox again, and I've got one more ask. Sparkle
Q. Redberry has fumbled a task. Git pull and merging, she did all the day; With
all this gitting, some creds got away. Urging - I scolded, "Don't put
creds in git! "She said, "Don't worry - you're having a fit. If I did
drop them then surely I could, Upload some new code done up as one should.
"Though I would like to believe this here elf,I'm worried we've put some
reds on a shelf. Any who's curious might find our "oops, "Please find
it fast before some other snoops! Find Sparkle's password, then run the
runtoanswer tool.
ii.
Key: twinkletwinkletwinkle
iii.
Steps:
1.
Location of git "Which git"
a.
Log into Cranberry Pi system and drop into the
/usr/elf/kccongmgmt directory
b.
Run "git log -p" to see changes made
over the commit history
i.


c.
Read through the various levels of commit.
Spotted a url API login credentials scheme: mongodb://username:password@127.0.0.1:27017/node-api
i.


d.
In a later commit, we see the string that logs
into the node-api as Ms. Sparkle Redberry: url' :
'mongodb://sredberry:twinkletwinkletwinkle@127.0.0.1:10073/node-api
i.


e.
Edited out of the git log, and ran ./runtoanswer
twinkletwinkletwinkle
i.
![Applications
Places Firefox ESR
Mon 17:07
Holiday Hack Challenge 2018 - Mozilla Firefox
Holiday Hack Challem X O My simply Git Cheatshee X
Don't publicly expose .git X +
@ https://kringlecon.com/?modal=challenge&rid=56b32063-a644-4048-8203-a089dd842b94&challenge=gitpasshist
Most Visited SQL Injection Bypassin... @ Offensive Security @ Kali Linux @ Kali Docs
Kali Tools @ Exploit-DB Aircrack-ng @ Kali Forums @ NetHunter @ Kali Training Getting Started
lil\ O
Jyrclla
head>
<title>Conference API</title>
<link rel=" //netdna . bootstrapcdn . com/font-awesome/4. O. 3/css/font-
awesome. min . css
Imodpm
Sugarplum Mary
rmalick
fancysauce
tedster1999
New [Achievement] Unlocked: Dev Ops Fail!
Click here to see this item in your badge.
E-dqeWi
perih'A
Dev OOS
<link
eboilerplate
<link
rel=" stylesheet"
<link
rel=" stylesheet"
<link
rel=" stylesheet"
<link
rel=" stylesheet"
<link
rel=" stylesheet"
<link
rel=" stylesheet"
<link
rel=" stylesheet"
href=" /bower
h ref=" /bower
h ref=" /bower
href=" /bower
href=" /bower
h ref=" /bower
h ref=" /bower
components/ responsiveboilerplate/css/ responsiv
components/ pu recss/src/base/css/base. css
components/ pu recss/src/buttons/css/buttons . css
components/purecss/src/buttons/css/buttons-cor
components/pu recss/src/forms/css/forms . css
components/ pu recss/src/menus/css/menus . css
components/ pu recss/src/menus/css/menus - core. cs
href=" /stylesheets/ma rketing . css
cd
elf@fOe8c35f1507. —/kcconfmgmt$
elf@foe8c35f1507
. / runtoanswer
Loading, please wait......
Enter Sparkle Redberry's password:
I'm sorry, that is not the right answer.
elf@foe8c35f1507
. /runtoanswer
Loading, please wait......
Enter Sparkle Redberry's password: twinkletwinkletwinkle
his ain't "I told you
so" time, but it's true:
I shake my head at the
goofs we go through.
Everyone knows that the gits aren't the place;
Store your credentials in some safer space.
Cong ratulations !
If@foe8c35f1507. -$
Close
Henooo! Type here to chat.
Sparkle Redberry
Hi, I'm Sparkle Redberry!
Ugh, can you believe that Elf Resources is poking
around? Something about sensitive info in my git repo.
I mean, I may have uploaded something sensitive
earlier, but it's no big deal. I overwrote it!
Care to check my Cranberry Pi terminal and prove me
right?
Hi, I'm Sparkle Redberry!
Ugh, can you believe that Elf Resources is poking
around? Something about sensitive info in my git repo.
I mean, I may have uploaded something sensitive
earlier, but it's no big deal. I overwrote it!
Care to check my Cranberry Pi terminal and prove me
right?
Hi, I'm Sparkle Redberry!
Ugh, can you believe that Elf Resources is poking
around? Something about sensitive info in my git repo.
I mean, I may have uploaded something sensitive
earlier, but it's no big deal. I overwrote it!
Care to check my Cranberry Pi terminal and prove me
right?
Hi, I'm Sparkle Redberry!](file:///C:/Users/chris/AppData/Local/Temp/msohtmlclip1/01/clip_image064.png)
![Applications
Places Firefox ESR
Mon 17:07
Holiday Hack Challenge 2018 - Mozilla Firefox
Holiday Hack Challem X O My simply Git Cheatshee X
Don't publicly expose .git X +
@ https://kringlecon.com/?modal=challenge&rid=56b32063-a644-4048-8203-a089dd842b94&challenge=gitpasshist
Most Visited SQL Injection Bypassin... @ Offensive Security @ Kali Linux @ Kali Docs
Kali Tools @ Exploit-DB Aircrack-ng @ Kali Forums @ NetHunter @ Kali Training Getting Started
lil\ O
Jyrclla
head>
<title>Conference API</title>
<link rel=" //netdna . bootstrapcdn . com/font-awesome/4. O. 3/css/font-
awesome. min . css
Imodpm
Sugarplum Mary
rmalick
fancysauce
tedster1999
New [Achievement] Unlocked: Dev Ops Fail!
Click here to see this item in your badge.
E-dqeWi
perih'A
Dev OOS
<link
eboilerplate
<link
rel=" stylesheet"
<link
rel=" stylesheet"
<link
rel=" stylesheet"
<link
rel=" stylesheet"
<link
rel=" stylesheet"
<link
rel=" stylesheet"
<link
rel=" stylesheet"
href=" /bower
h ref=" /bower
h ref=" /bower
href=" /bower
href=" /bower
h ref=" /bower
h ref=" /bower
components/ responsiveboilerplate/css/ responsiv
components/ pu recss/src/base/css/base. css
components/ pu recss/src/buttons/css/buttons . css
components/purecss/src/buttons/css/buttons-cor
components/pu recss/src/forms/css/forms . css
components/ pu recss/src/menus/css/menus . css
components/ pu recss/src/menus/css/menus - core. cs
href=" /stylesheets/ma rketing . css
cd
elf@fOe8c35f1507. —/kcconfmgmt$
elf@foe8c35f1507
. / runtoanswer
Loading, please wait......
Enter Sparkle Redberry's password:
I'm sorry, that is not the right answer.
elf@foe8c35f1507
. /runtoanswer
Loading, please wait......
Enter Sparkle Redberry's password: twinkletwinkletwinkle
his ain't "I told you
so" time, but it's true:
I shake my head at the
goofs we go through.
Everyone knows that the gits aren't the place;
Store your credentials in some safer space.
Cong ratulations !
If@foe8c35f1507. -$
Close
Henooo! Type here to chat.
Sparkle Redberry
Hi, I'm Sparkle Redberry!
Ugh, can you believe that Elf Resources is poking
around? Something about sensitive info in my git repo.
I mean, I may have uploaded something sensitive
earlier, but it's no big deal. I overwrote it!
Care to check my Cranberry Pi terminal and prove me
right?
Hi, I'm Sparkle Redberry!
Ugh, can you believe that Elf Resources is poking
around? Something about sensitive info in my git repo.
I mean, I may have uploaded something sensitive
earlier, but it's no big deal. I overwrote it!
Care to check my Cranberry Pi terminal and prove me
right?
Hi, I'm Sparkle Redberry!
Ugh, can you believe that Elf Resources is poking
around? Something about sensitive info in my git repo.
I mean, I may have uploaded something sensitive
earlier, but it's no big deal. I overwrote it!
Care to check my Cranberry Pi terminal and prove me
right?
Hi, I'm Sparkle Redberry!](file:///C:/Users/chris/AppData/Local/Temp/msohtmlclip1/01/clip_image064.png)
mongodb://sredberry:twinkletwinkletwinkle@127.0.0.1:10073/node-api
Subscribe to:
Comments (Atom)